I received an e-mail today at my work address with the subject [Feature Ideas [Customers Only]] - [Survey] The G Suite Admin Experience team wants to learn your needs around data/resource access boundaries
which looked like the following:
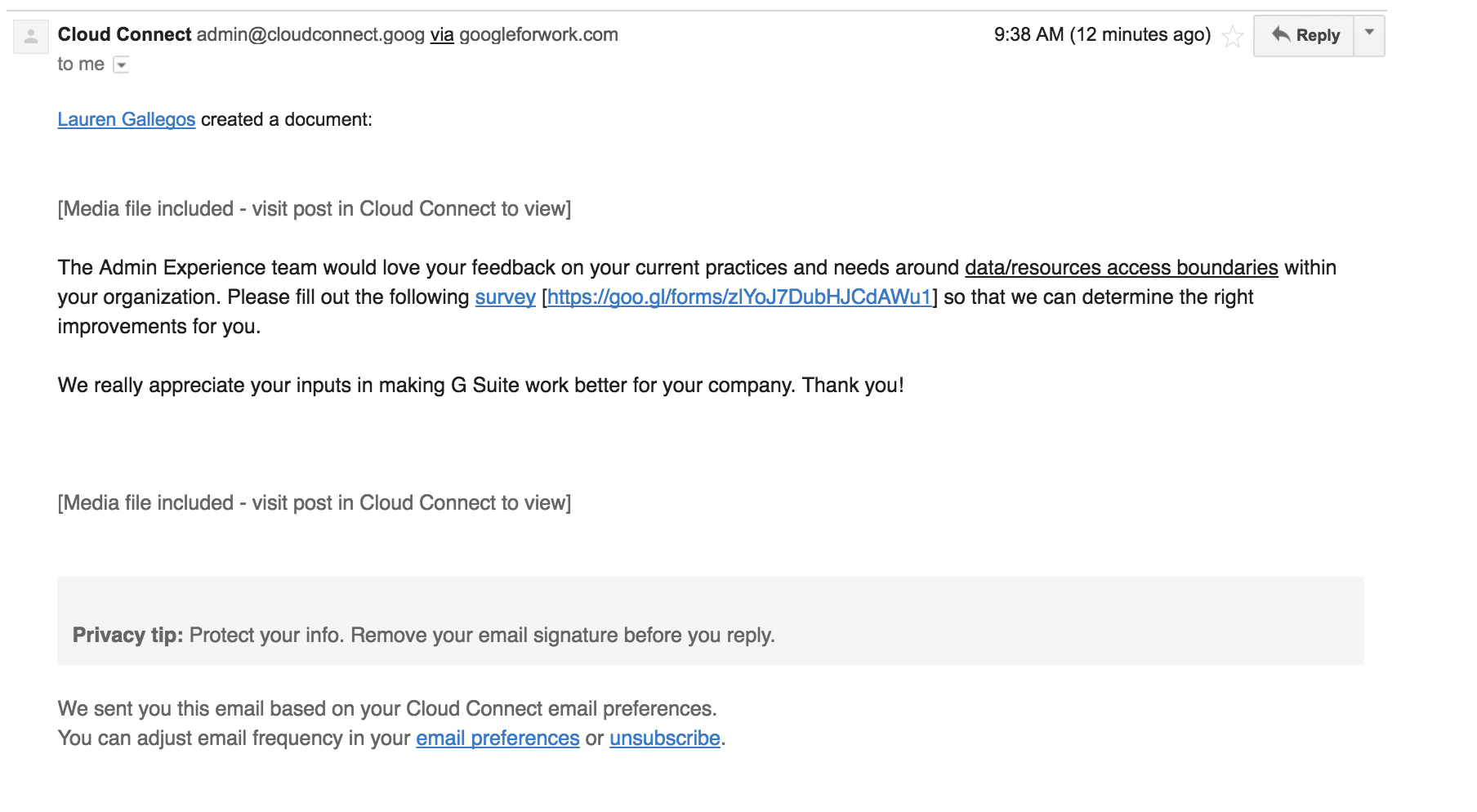
Quick — is this real or is this spam? What would you look for?
Me, the first thing I'd look for is a source address that matches a domain I trust. Then I'd confirm via SPF and DKIM that the e-mail was from a valid sender in that domain. Well, let's take a look here... cloudconnect.goog; I don't know what the hell that domain is. I guess .goog is a gTLD that got delegated on 24 January 2015. It's operated by servers run by charlestonroadregistry.com, which is Google's private domain registrar. Google doesn't seem to use .goog for anything official; they always use the .google gTLD in other communications. Let's check WHOIS:
% whois cloudconnect.goog
whois: goog.whois-servers.net: nodename nor servname provided, or not known
Okay... That's neat...
As you can verify yourself, cloudconnect.goog points (in DNS) to a Google IP address, but whatever server as at that IP address doesn't seem to know anything about cloudconnect.goog...
Well, let's check some headers
| Header Name | Header Value |
|---|---|
| Received-SPF | pass (google.com: domain of no-reply@googleforwork.com designates 204.93.64.117 as permitted sender) client-ip=204.93.64.117; |
| Authentication-Results | mx.google.com; spf=pass (google.com : domain of no-reply@googleforwork.com designates 204.93.64.117 as permitted sender) smtp.mailfrom=no-reply@googleforwork.com |
| Message-ID | 59c299a2.0766620a.3494d.be26SMTPIN_ADDED_BROKEN@mx.google.com |
| X-Google-Original-Message-ID | <102-21263-3-17686-1505925336940.google.jivemailuser@https://www.cloudconnect.goog> |
| From | Cloud Connect admin@cloudconnect.goog |
| Reply-To | google-982964215-37db-2u-gen@google-enterprise-connect-v8.hosted.jivesoftware.com |
| X-Jive-Office | google-982964215-37db-2u-gen@google-enterprise-connect-v8.hosted.jivesoftware.com |
If you don't read SMTP headers natively, this tells us that it was sent from someone originally claiming to be no-reply@googleforwork.com using a tool called Jive and was rewritten to this cloudconnect.goog address. Jive appears to be software that's directly in competition with Gsuite/Google Apps, so that's another point in favor of this being not legitimate.
Notably, there's no DKIM signature on this message. The domain cloudconnect.goog has no published DMARC entry telling us to expect a DKIM signature, but still, that's just bad form. There is a passing SPF record, although it just looks like googleforwork.com has allowed all mail sent through Jive (which is the owner of 204.93.64.117). It would be interesting to see if Jive has reserved that outbound address for Google's use only (if this is, in fact, Google) or whether any customer can pass this SPF check...
Okay, so we've got no useful information on cloudconnect.goog, and that's just the From header only, which is spoofable. Let's check out the thing that SPF is actually identifying, googleforwork.com
% whois googleforwork.com
Domain Name: GOOGLEFORWORK.COM
Registry Domain ID: 1832269821_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.markmonitor.com
Registrar URL: http://www.markmonitor.com
Updated Date: 2016-09-21T09:22:11Z
Creation Date: 2013-10-23T20:56:04Z
Registry Expiry Date: 2017-10-23T20:56:04Z
Registrar: MarkMonitor Inc.
Okay, that's owned by MarkMonitor. MarkMonitor is used by lots of big companies for domain registration, so that doesn't tell us much (although most Google properties list Google as the registrar, not MM).
The DNS records for googleforwork.com point to a Google property, but that doesn't really tell us much. Anybody can point DNS at anything.
Maybe SSL?
% openssl s_client -connect www.googleforwork.com:443
CONNECTED(00000003)
depth=2 /C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
verify error:num=20:unable to get local issuer certificate
verify return:0
---
Certificate chain
0 s:/C=US/ST=California/L=Mountain View/O=Google Inc/CN=*.google.com
i:/C=US/O=Google Inc/CN=Google Internet Authority G2
1 s:/C=US/O=Google Inc/CN=Google Internet Authority G2
i:/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
2 s:/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
i:/C=US/O=Equifax/OU=Equifax Secure Certificate Authority
---
That's a little better... This is serving a certificate which has both *.google.com and *.googleforwork.com in it. That's the first sign that this domain actually belongs to Google and isn't Phishing.
Conclusions
I've been doing ops work for, like, 12 years now. I've been doing information security work for much of that time. I'm intimately familiar with the details of e-mail security.
It took me almost half an hour to fail to come to a conclusion on whether or not this is phishing.
This is incredibly bad. If this is phishing, it's really good (and was able to get a checkmark in Gmail). If it's not phishing, then Google, what the hell are you doing!? Whoever sends e-mails like this needs to be put into a remedial class on how e-mail trust works and a grown-up needs to take over for them. If any of the readers of this post work internally and can find out how trust in the Gsuite team got so screwed up, I'd love to know.
Want to comment on this? How about we talk on Mastodon instead? Share on Mastodon
Share on Mastodon